Ransomware guideline
Introduction
This guideline discusses ransomware and the Queensland Governments position against paying ransomware. It also discusses ways that agencies can protect themselves and outlines the processes agencies should take when impacted by ransomware.
This document provides information and guidance for Queensland Government entities and is for information only. While some information communicates other mandatory obligations which may be relevant in the context of the Information and cyber security policy (IS18), departments are strongly recommended to further investigate these obligations in-light of their own business requirements and seek legal/expert advice where necessary.
Audience
This document is intended for all Queensland Government departments, local government, government-owned corporations and statutory entities, including but not limited to:
- chief information security officers
- chief information officers (CIOs)
- information security officers
- risk management committees
- information management directors and managers
- information owners/custodians
- cyber security strategists and policy officials.
What is ransomware?
Ransomware is a common form of cybercrime, whereby a cybercriminal renders data inaccessible through encryption. The victim receives a ransom demand from the cybercriminal and in return a decryption key is provided to allow recovery of the encrypted data. Sensitive data is often stolen with a threat of public release to provide further incentive to pay the demand. In exchange for a ransom, the cyber criminal promises to provide code to allow the victim to regain access to their system or information.
Ransomware attacks began to soar in popularity with the growth of cryptocurrencies, such as Bitcoin. Cryptocurrency is a digital currency that uses encryption techniques to verify and secure transactions and control the creation of new units.
The steps of a ransomware attack
There are generally five steps to a ransomware attack which are outlined below:
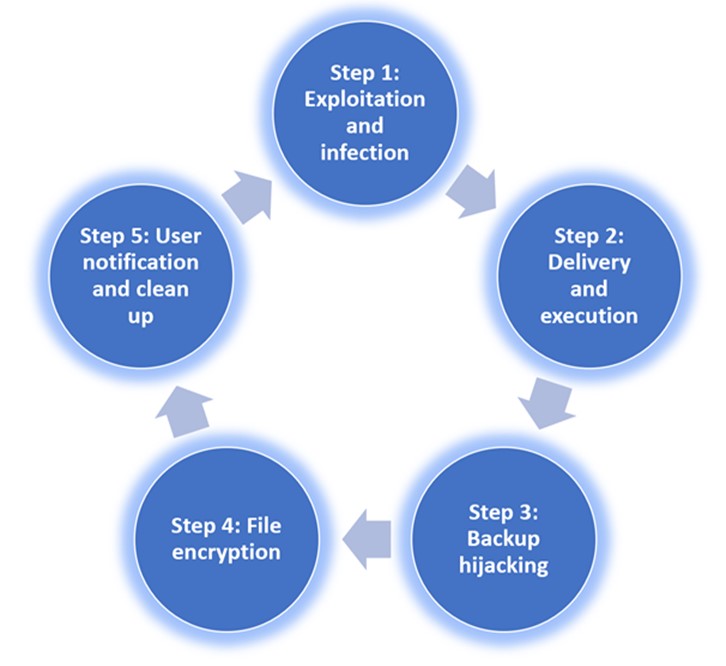
Step 1: Exploitation and infection - For the attack to be carried out, the ransomware file needs to be downloaded on a computer. This often occurs through a phishing email or a malicious exploit kit code.
Step 2: Delivery and execution - During this phase, the actual ransomware is delivered to the victims device. After downloading it, persistence mechanisms are implemented. Some of the delivery methods are:
- Spear phishing - where the victim receives an attachment or link that they click
- Drive-by phishing campaign - where an attacker can exploit a vulnerability in the web browser or related applications
- Exploitation - where an attacker can exploit a vulnerability and gain access to a remote system or allow the ransomware to propagate automatically
- Replication through removable media - this includes networked media that ransomware encrypts at the same time as it infects the victim
- Valid accounts - where an attacker has valid credentials to the target system and can authenticate to it.
From there, attackers will use common techniques for execution, typically through:
- Command-Line Interface / Graphical-User Interface
- PowerShell
- Scripting
- User execution.
Step 3: Backup hijacking - Shortly after, the malware attacks the files and folders with backup copies in the victims system and deletes them to ensure that the backup copies cannot be used to recover the data. This is unique to ransomware: other fraudulent software does not eliminate backup files.
Step 4: File encryption - Once the backup files are deleted, the malware performs a secure key exchange with the command-and-control server (C2). This establishes the encryption keys which will be used in the local system.
Step 5: User notification and clean up - After the backup copies are deleted and encryption is complete, the user receives instructions on how to recover their data, and they are coerced into making a payment (usually in bitcoin). Generally, a company will be given a few days to make the payment, after which the amount will increase.
Should a ransom be paid?
The Australian Governments ransomware action plan 2021, together with the Australian Governments Ransomware Payments Bill 2021 has highlighted the importance of this issue.
The Queensland Government adopts the advice of the Australian Cyber Security Centres (ACSC) to not pay the ransom as there is no guarantee it will fix the issue and can increase the likelihood of future attacks. The ACSC reiterates the importance of effective cyber security practices and the need to back up data.
The payment of ransoms encourages the spread of the ransomware business model and increases targeting of the government sector. For this reason, it is almost always unethical to pay ransomware demands even if the cost of remediation is greater than the ransom.
There are other considerations:
- Payment of ransoms rewards criminal behaviour; in some cases, it may support the financing of ongoing terrorist activity.
- There is no guarantee that an agency will get its data or files back - other than the word of the cybercriminal. The ransomware business model relies on its reputation, but payment does not guarantee data will be returned.
- Agreeing to pay suggests to the cybercriminal that the agency hasn't backed up files - which may increase the ransom price or target the agency for 'another round' of ransomware.
- Involving law enforcement may allow police to use legal authorities and tools that are unavailable to the public and organisations to help catch cybercriminal.
- In some cases, law enforcement may have ransomware keys that have been recovered from other attacks or via a key repository such as nomoreransom.org. (Opens in new window)
What to do if subject to a ransomware?
If an agency is subject to a ransomware demand and/or is considering paying a ransomware, are strongly encouraged to contact the Queensland Government Cyber Security Unit (CSU) and report this as an incident in line with the Information security incident reporting standard under the Information and cyber security policy (IS18).
Use any of the following communications channels:
- Phone: 07 3215 3951
- Email QGISVRT: qgisvrt@qld.gov.au
- Email General: cybersecurityunit@qld.gov.au
The CSU facilitates and supports cyber information and intelligence monitoring capabilities to identify potential threats to Queensland and other jurisdictions. CSU plays a coordination role and is responsible for:
- collecting, assessing and communicating cyber intelligence
- briefing Queensland Government Ministers and agencies
- liaising with the Australian Cyber Security Centre
- liaising with Queensland Police Services
- managing public communications
- developing and reviewing incident response strategies.
Prevention and management of a ransomware incident
Ransomware is just one type of security incident, and as such should align to general incident management processes as stated in the QGEA Incident management guideline. Specific guidance related to ransomware (aligned to incident management processes) is as follows:
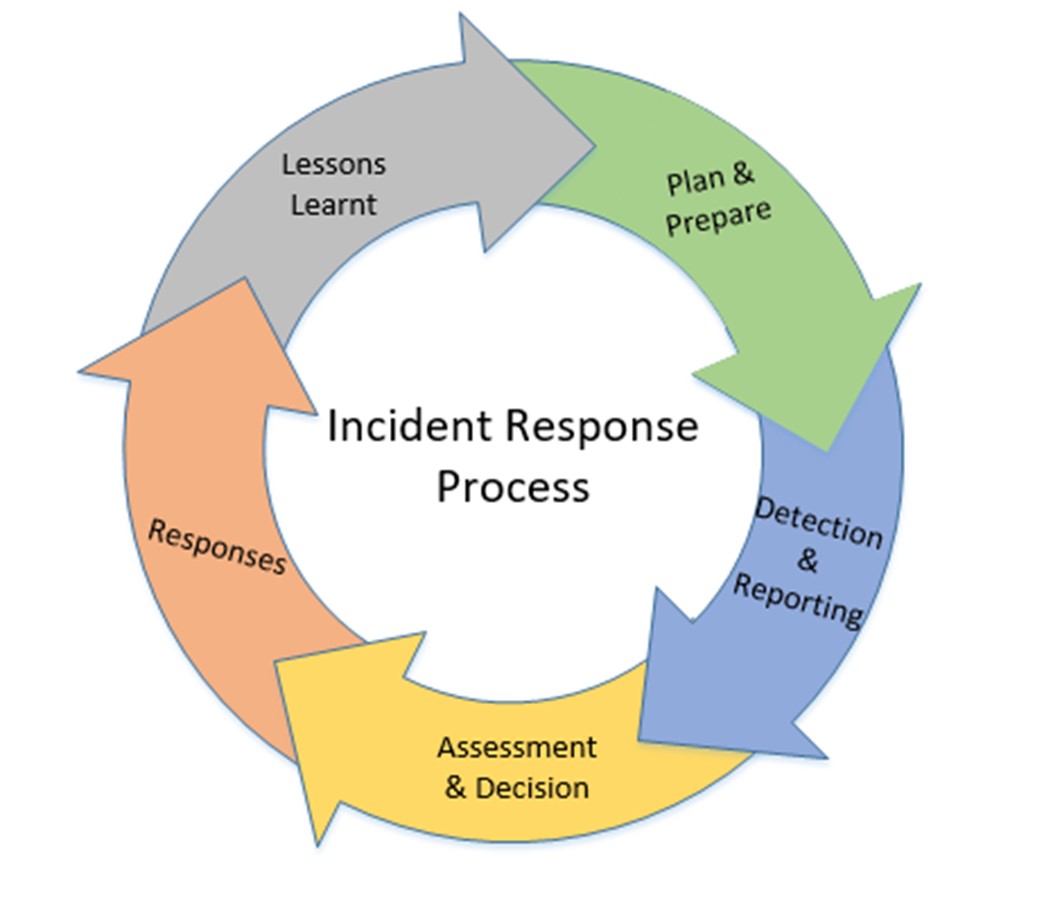
Plan and prepare
The objective is to prepare the department to respond to ransomware incidents in an effective and timely manner. To ensure staff are informed of their roles in containing and mitigating a Ransomware, and to ensure reporting mechanisms are in place.
Recommended preparatory activities that should be completed in this phase are detailed below.
Key activities
- Plan your organisations information security to enhance protection of your network infrastructure, storage, and media devices and systems:
- Develop your backup plan:
- Use a Backup appliance monitoring tool
- Observe what your usual incremental backups are, and beware of abnormal changes
- Apply all security patches on your backup
- Create isolated copy of your backup data
- Audit access rights on your backups, to ensure write privileges are limited
- Consider the use of Role Based Access controls
- Turn on Multifactor Authentication (MFA).
- Develop your department or agencies incident response plan and playbook
- Develop your department or agencies recovery plan to complement your incident response and backup plans
- Establish a process to manage your department or agencies user and administrator accounts
- Prepare to:
- Review and rehearse your organisations incident response procedures to validated key technical and business roles and responsibilities
- Define how frequent your organisation should rehearse the Incident Response procedure, and involve all key stakeholders as planned during emergency
- Escalation to major incident management, where appropriate establish the QGCSA levels and reporting procedure
- Have offline copies of your documentation
- Establish an out-of-band communication, remote access, and file transfer capability
- Establish and maintain regular vulnerability and patch management process
- Predetermine:
- Insurance stance
- Recovery how, criticality order and timing
- Workout what might be rebuilt differently,
- What legal requirements/reporting obligations are likely,
- How to determine date trust,
- What 3rd parties and providers may be involved; and
- Resourcing allocation.
- Pre-approve your department or agencies incident response support requirements:
- Security appliances installed on network
- Domain admin account (setup and disabled)
- Network and systems access for incident responders
- Network and systems access for external security partners.
- Ensure disposal equipment are sanitised
- Review recent incidents result and lessons
- Review your organisations cyber threat intelligence (CTI) and monitor for threats to your agency, common vulnerabilities, newly developed risks, as well as your 3rd party risks
- Define indicators for both threat and risk, and develop an alerting pattern within your organisations SIEM solution
- Educate staff:
- By conducting regular security awareness campaigns to address common information security risks faced by employees, such as:
- Phishing attacks:
- Exercise with custom phishing templates that involve the applications and systems that your organisation uses
- Malicious emails or business email compromise
- Ransomware
- How to report suspected cyber incidents
- Phishing attacks:
- Mandating regular security training for all staff, especially for those managing personal, confidential, or high-risk data and systems
- Participate in Whole-of-Government Cyber Exercises such as Redhawke to practice and assess your organisations internal processes and procedures.
- By conducting regular security awareness campaigns to address common information security risks faced by employees, such as:
Refer to appendix A on ransomware preparedness, for an actionable checklist to prepare and protect your environment against ransomware attacks.
Detection and reporting
A department should employ mechanisms to detect and report breaches of the confidentiality, integrity, and availability of its data. Ensure resources to undertake and complete initial investigation of the Ransomware, and to ensure incidents are formally reported to the relevant team.
Key activities
- Detect and report the incident:
- First ensure setup for monitoring and logging capability for your systems and networks are in place, and alerts are automated and received by the appropriate team
- Consider implementing an Endpoint Detection and Response (EDR) solution to detect and block suspicious activities and system behaviours, and gain valuable information on your systems
- Monitor all detection channels, including customer and staff channels, social media and cyber threat intel feeds for indications of data breach
- Maintain updated contact information for reporting incidents
- Have a process of tracking incidents from its detection until its closure e.g., service desk ticketing system with assigned personnel and business area
- Consider whether data loss or data breach has occurred and utilise your internal processes or playbook for managing data breaches
- Classify the incident as per the available information related to the data loss and incident types
- Report the information security incident in accordance with the information security incident response guidelines
- Consider the intelligence value to other departments, agencies or other government entities alike and share on the relevant channels
- Consider the scale of the compromise and manage your team accordingly
- Ensure backups are protected
- Where appropriate consider notification requirements:
- Briefing for the relevant Minister ore Premier
- Queensland Government Cyber Security Unit (QGCSU)
- Australian Cyber Security Centre (ACSC)
- GDPR for Europe
- Regulatory bodies etc.
- Initial Investigation of the incident:
- Assemble your departments information security incident response team (ISIRT) to begin initial investigation of the incident (ensure you have updated team details)
- Identify likelihood of widespread of the Ransomware infection
- Stop your backup system from further backups, and immediately isolate all your business-critical assets (crown-jewels), servers and applications to avoid contamination
- Generate a SITREP report, at a minimum information such as:
- Type of incident
- How was the incident detected?
- Where are Ransomware messages appearing
- Identify the attack email
- The detection location physical and logical
- Initial number of affected assets across the organisation, and ascertain whether its spreading
- Any other additional reporting relating to affected assets, including system and event logs, network monitoring logs, AV logs
- Establishing business impact, and any initial action being undertaken.
- Advise helpdesk staff or staff on reception duties on the confrontational tactics the adversary may employ and prepare them in advance
- Secure artefacts, including copies of suspected malicious software and forensic copies of affected systems for future analysis
- Research Cyber Threat Intelligence sources and consider accessing the ACSC and QGCSU capabilities to gain further intelligence and support mitigation
- Review the incident categorisation to validate it is a Ransomware type incident, and assess the incident priority, based upon the initial investigation
- Establish the requirement for a full forensic investigation:
- Engage Queensland Police Services (QPS) at the initial stage of the incident to avoid tampering with important evidence
- Evidence handling should be done in line with the Queensland Police Services investigative process (Opens in new window) .
Assessment and decision
This is the analysis stage of the information security incident management phases. A department should look to examine the scope of the incident i.e., ransomware attack. To identify, evaluate and report potentially breached data and the impact to the organisation. Departments should have or establish forensic investigation requirements and determine plans for incident remediation as per the scope and investigation of the incident.
Key activities
- Analyse the extent and the business impact of the Ransomware incident:
- Engage your internal incident response team to establish the scope and document an initial understanding of what has occurred
- Classify and determine the type and ransomware family by exposure to multiple AV tools
- Scope the ransomware attack to include information on:
- Where are ransom messages appearing?
- Identify the attack email or entry point and the extend of travel
- Establish an understanding of its spread, and whether disconnecting devices from the network is the best and necessary option to avoid further spread.
- Analyse the Ransomware:
- First execute the Ransomware in a secure environment, segregated from the business network:
- Understand its mechanisms, and the functionality it implements
- Determine the ransomware behaviour on a test system, with understanding of things like created files, launched services, modified registry keys and network communications.
- First execute the Ransomware in a secure environment, segregated from the business network:
- Identify and report potentially compromised data and systems:
- Review affected infrastructure within your environment for indicators of compromise derived from the malware or ransomware analysis, so that additional compromised systems are identified
- Identify any data assets impacted by the ransomware attack, including data in motion
- Triage and prioritise impacted systems for restoration and recovery during the remediation or response phase:
- Prioritise restoration and recovery as per a predefined critical asset list, including critical information systems related to health and safety, systems for revenue generation, and other systems those critical services are dependent on
- Review cyber threat intelligence feeds to determine whether the ransomware attack is targeted at specific accounts, systems and infrastructure
- Verify all infected critical information and system assets are in the process of being recalled and quarantined
- Monitor systems that are not deemed impacted so they are deprioritised for remediation.
- Engage asset owners and the business or management team to understand the business impact of the compromise:
- Have a dedicated resource to help with communication between the business or senior management team and IT team include your internal communication team in this process.
- As required, report the information security incident to the organisations senior management:
- Maintain a SITREP report
- Establish the likelihood that identified datas confidentiality, integrity or availability was breached
- Confirm trust of domain controllers and authentication systems
- Confirm security of known good backups
- Consider reporting to Queensland Police Service (QPS)
- Update senior management of any suspected and confirmed data breach, including the unauthorised access to personal or sensitive departmental data
- Report any suspected and confirmed data breach, including data related to your third-party suppliers, and customers, for agencies that manages client data.
- Develop remediation plan:
- Incorporate both technical and business analysis to determine remediation priorities
Responses
As the remediation or ransomware mitigation stage of the information security incident response processes, departments should assume threat actors have visibility into their network environment and therefore, it is recommended to use alternate communication mechanisms (e.g., external email accessed via devices that are not connected to the compromised network) to coordinate the response procedures. The coordination will include key actionable steps necessary to contain the ransomware effect and impact, eradicate the ransomware through agreed mitigation procedures, and to recover targeted systems and services to their normal operational state (BAU state).
Refer to appendix B on ACSC ransomware guide checklist for an immediate response action.
Key activities
- Containment:
- Determine infected areas within the organisations network for isolation, and contain the technical mechanisms of the ransomware attack:
- Minimise further malicious activity by quarantining affected systems and removing them from the network, where possible, or applying access controls to isolate from production networks
- Reset impacted users or host credentials
- Secure copies of the malicious code, affected systems and any identified artefacts for further investigation
- Establish protection measures derived from the results of malicious code analysis to protect your environment from the ransomware and malicious activity alike
- For preservation of evidence, capture an image sample of the affected devices (workstations and servers), system and memory image.
- Collect any relevant system logs, samples of the malware and associated indicators of compromise e.g., suspicious registry entries
- Define scope by searching for SHA-1 process name, the executable file name, any relevant URL or IP address of similar connections on the network
- Where necessary work in partnership with your vendors and 3rd Party providers or suppliers to obtain the necessary logs, submit samples of malicious code for deeper analysis. Ensure SLAs and KPIs are met
- Notify the Queensland Government Cyber Security Unit and ACSC with an initial situational report
- Engage Queensland Police Service (QPS) with the evidence containment and handling procedure for further analysis.
- For a ransomware incident involving email compromise:
- Block the sender and the message by marking it as spam
- Block the IP address identified in the email header.
- For a ransomware incident involving a website compromise:
- Block the at the network perimeter
- Sinkhole the domain on internal DNS servers
- Block the sites IP address on the network firewall
- Ensure all used web browsers have the latest patches.
- Ensure your organisations security awareness program addresses basic security hygiene for IT equipment and system use
- Block access to any identified Remote Access Tools to prevent communication with command-and-control servers, websites and exploited applications
- Notify business data owners and relevant stakeholders of the progress containment activities
- For the benefit of evidence gathering (e.g., forensic investigation), remind staff to move the attack email to the Junk folder. No evidence should be deleted or tempered with throughout the incident response cycle or process
- Run quick validation checks on integrity of data backups.
- Determine infected areas within the organisations network for isolation, and contain the technical mechanisms of the ransomware attack:
- Eradication:
- Remediate the point of entry:
- Identify removal methods from the results of the malicious code analysis and trusted sources.
- Use appropriate tools to complete the removal process to remediate ransomware or compromised executables
- Implement your departments backup and restoration plan:
- Ensure your departments backup are updated and ready for use
- Re-install any standalone systems from a clean OS backup before updating with trusted data backups
- Identify your restoration priorities, starting with your organisations critical systems and data
- Conduct a restoration of affected networked systems from a trusted backup
- Ensure changes are made to all compromised accounts credentials
- Verify the restoration of your organisations critical systems and data.
- Continue to monitor your cyber threat intelligence sources for signatures and other indicators of compromise to prevent further ransomware spread:
- Remediate the point of entry:
- Recover to BAU:
- Recover systems based on business impact analysis and business criticality follow a phased approach while you recover your critical systems, servers and applications
- Conduct complete ransomware scanning of all systems across your department
- Re-image systems to their normal working state
- Re-set the credentials of affected systems and users account details
- Reconfigure previously compromised systems
- Restore any corrupted or destroyed data
- Restore any suspended services
- Continue to monitor your environment to detect any potential suspicious activity
- Co-ordinate and verify the successful implementation of any necessary patches or vulnerability remediation activities
- Track patching SLAs ensuring critical vulnerabilities have undergone risk assessment and act on within 48hr of detection
- Seek professional assistance from a reputable cyber incident response company.
Lessons Learnt
The last phase of the incident response process that takes place at the end of the ransomware incident resolution. Having analysed, evaluated, and documented the ransomware incident and its resolution, department should take the time in this stage to ensure post incident response is conducted. The objective is to draw lessons learnt from the incident, discuss areas of improvement, to incorporate recommended actions to improve their incident management plans and other controls.
Key activities
- Incident reporting:
- Prepare a post-incident report to include at a minimum the following details:
- Details of the cause, impact and actions taken to mitigate the ransomware incident, including timeline of activities, type and location of incident, as well as the effect on systems, network devices and users
- Activities undertaken by relevant resolver groups, service and third-party providers, and business stakeholders
- Recommendations where any aspects of people, process or technology could be improved across the organisation to help prevent a similar information security incident from reoccurring, as part of a formalised lessons identified process.
- Based on the lessons learnt, prepare a best practice advisory for your end-users (to include both technical and non-technical staff)
- Package and share your recent incident response with QGCSU to be utilised for Whole-of-government cyber exercise.
- Prepare a post-incident report to include at a minimum the following details:
- Post Incident Review (PIR):
- PIR should cover the complete summary and review of all the actions and review during the incident response process, including
- Lessons identified and problem management:
- Complete the formal lessons identified process to feedback into future preparation activities
- Consider sharing lessons identified with the wider Queensland Public Sector
- Consider capturing these key lessons to be incorporated into your future cyber security exercises for training and awareness purpose
- Conduct root cause analysis to identify and remediate/mitigate underlying vulnerabilities.
- Lessons identified and problem management:
- PIR should cover the complete summary and review of all the actions and review during the incident response process, including
- Communication:
- Publish internal communications to inform and educate employees on ransomware attacks and security awareness:
- Have training focused on the channel that was exploited during recent cyber-attacks or incidents
- As part of the lessons learnt, design custom phishing templates to build on the skill gaps.
- Publish external communications, where appropriate, ensure your internal media communication processes are in-line with Queensland Government Cyber Security Arrangement Operational and Hazard plan communication strategy:
- To establish whole-of-government picture and to ensure the management of information in a unified manner
- To provide advice to customers, engage with the market, and inform and engage media and the pubic of the information security or cyber incident.
- Ensure these communications touched on key information about the information security incident (ransomware attack) without leaving the organisation, government critical assets or the public vulnerable to further ransomware attacks.
- Publish internal communications to inform and educate employees on ransomware attacks and security awareness:
Further reading
- Incident Management Guideline
- Information Security Incident Reporting
- Ransomware by ACSC (Opens in new window)
- Protect yourself against ransomware attacks(Opens in new window)
- Essential Eight (Opens in new window)
Appendix A ACSC Ransomware Action Checklist
QGCSU recommends filling out this checklist to ensure your department is ready for a ransomware attack.
Action | If you experienced a ransomware attack, was this enabled at the time? | Is this enabled now? | Devices enabled on | Set up by | Date set up | |
Update your device and turn on automatic updates | Yes | No | Yes | |||
Turn on two-factor authentication | Yes | No | Yes | |||
Setup and perform regular backups | Yes | No | Yes | |||
Implement access controls | Yes | No | Yes | |||
Turn on ransomware protection | Yes | No | Yes | |||
Prepare your Cyber Emergency checklist | Yes | No | Yes | |||
Table 1 Ransomware Action Checklist
Source: www.cyber.gov.au
Appendix B ACSC Ransomware Guide Checklist for an immediate response action
This checklist guides you through simple ways you can limit the damage caused by ransomware.
Steps | Action | Detailed action |
1 | Disconnect the device | Immediately disconnect the infected device from the internet, other networks and external storage devices to disrupt the potential spread of ransomware |
2 | Stop the ransomware | Use Task Manager on Microsoft Windows to force quit suspicious or unwanted activity on your device |
3 | Malware scan and removal | Use your devices malware scanner to find and remove any malware including ransomware. This may take several hours |
4 | Note down key details | Record details while it is still fresh in your mind for better outcomes. This will help with further assistance you may require |
5 | Get professional assistance | Professional incident response service providers could help you with backing up your data, resetting your device(s) and restoring your files. |
6 | Notify and report | If your agency holds sensitive information (such as financial or personally identifiable information) you may have to notify your customers and authorities: agencies should report the incident to ACSC through ReportCyber at cyber.gov.au, and to QGCSU at CyberSecurityUnit@chde.qld.gov.au Use the incident reporting spreadsheet for your report. |
7 | Protect yourself from future attacks | Read the ACSCs guide on Ransomware to help avoid this happening again in the future |
Table 2 Ransomware Emergency Response
Source: www.cyber.gov.au