Information security assurance and classification guideline
Final | July 2018 | v1.0.0 | Public
Purpose
This guideline provides advice about the quantity and quality of information security assurance that is reasonable regarding the security of information at differing business impact levels.
As stated in IS18:2018 policy requirement 4, agencies must obtain suitable levels of assurance that their departments information is secure.
Departments are encouraged to issue their own information classification and assurance policy similar to the example provided at the end of this guideline. Issuing a policy based on the example provided would satisfy the ISO27001 requirement - A.8.2 Information Classification.
Objectives
IS18:2018 requires accountable officers obtain appropriate assurance for information and information assets based on criticality.
Information security assurance provides objective assessment as to the security of information. The most objective assurance comes from independent external assessment measured against international best practice.Lower levels of assurance can be achieved through management systems, internal assessment and audit.
It is generally not practicable, nor economically viable, to apply the highest levels of assurance to all information and information assets. Departments should consider a risk based approach, applying higher levels of assurance to higher criticality information and information assets.
An information asset may have different business impact levels (BILs) for each area. The BIL is an assessment of the business impact of a loss of confidentiality, availability and integrity for an information asset.This is further explained in the Queensland Government Information Security Classification Framework (QGISCF).
Using assigned BILs for information, departments rank the criticality of their information as either high, medium or low. The departmental rankings of information criticality are then used to assess what level of assurance should be applied.
The security assurance model has been developed to:
- provide confidence in protective security practices defined in IS18:2018 policy requirement1, agencies must implement an Information security management system (ISMS) based on ISO 27001:2013
- support risk-based decisions when applying assurance activities to information assets
- identify and inform corrective action for the management of information security.
Security assurance model
Security assurance provides accountable officers with a level of confidence that identified risks to information assets are being managed appropriately.
The level of assurance and the resources spent on achieving the level, should be equal with the associated BIL for the information asset.
Lower levels of assurance can be obtained through operation of the ISMS as required by IS18:2018 policy requirement 1, which includes senior management oversight, periodic management reviews, controls selection processes, a risk management framework and compliance activities.
Higher levels of assurance can be obtained through measurement and reporting of key risk indicators (KRIs) for the ISMS, internal and external audit, and independent certification.
Assurance activities should be aligned to the three lines of defence model in risk management, as shown in figure 1.
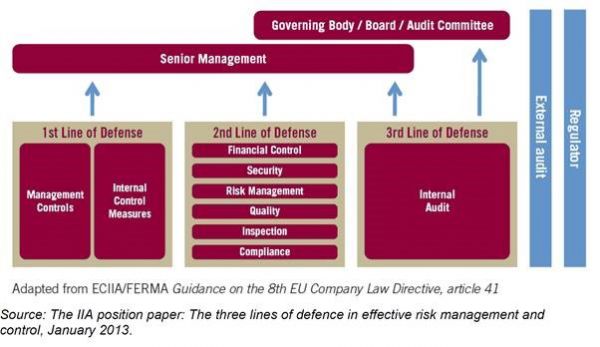
Assurance decision department policy
Implementing an information security assurance decision process requires the accountable officer to outline what levels of assurance are reasonable for differing criticalities of information. The departments Accountable Officer, advised by the executive leadership, should identify what levels of assurance are required of the department for different levels of information criticality in a departmental policy. An example of a departmental policy for information assurance is at Example. The policy is used to give effect to the assurance decision process.
Assurance decision process
Step 1 Business impact assessment
Use your organisational business impact levels (BILs) to establish the business impact for your information.
Higher levels of confidence should be obtained for information assets which represent greatest potential risk (business impact) to the organisation.
All information and information assets must be assigned an owner who is responsible for classification of the asset. To avoid duplication, agencies may apply their own endorsed method to determine the criticality/ significance of systems, as required. Agencies may also refer to the following to prioritise assurance activities:
Step 2 Evaluate appropriate assurance measures
There are significant variations across Queensland Government with respect to risk appetite and tolerance, budgets, operating environment, use of managed services, and legislative context.
Agencies may develop an assurance model that meets individual agency requirements, or draw from examples in the table below.
Business impact and assurance levels guideline
Business impact - > | Low | Medium | High |
|---|---|---|---|
Example - assurance measures | Self-attestation (ISMS Security Checklist) Audit by exception Periodic management review (ISMS) Vulnerability scanning | Cross government assurance Internal agency audit Regular management review Periodic penetration testing (e.g. every two years) | Maintaining certification to ISO 27001 External audit Frequent management review Regular penetration testing (e.g. minimum of once a year) |
Step 3 Select assurance measure(s)
The scope of the ISMS as defined by IS18:2018 policy requirement 1 includes all the information, application and technology assets. However, it is prudent to focus on the most critical information and assets.
Assurance activities should be selected at the discretion of the accountable officer and be included as inputs to the ISMS to demonstrate leadership and commitment, and to provide a level of confidence necessary for attestation of the accountable office for information security. The end purpose is to allow the accountable officer to confidently make an attestation to the security of their organisational information security.
Example
<<Department>> Information classification and assurance policy
- All information assets in << Department >> must be assessed for information security criticality against the <<Department>> Business Impact Levels and the QGISCF
- For each information asset in the <<Department>>, a single information security data custodian must be identified and assigned. Where there is no identified information security data custodian for a current asset, or a new information asset is acquired, one must be appointed as soon as reasonably practicable.
- The results from Business Impact Assessment for information assets must be reported to the Director-General through the <<Department>> Information Security Steering Committee
- Information assets that are of HIGH criticality storing, accessing, processing information that is:
classified PROTECTED, has a HIGH Integrity assessment, or has a HIGH Availability assessment- must undergo a yearly independent external assessment of the control environment against the requirements of ISO 27001:2013
- the data custodian must be member of the Queensland Senior Executive Service
- Information assets that are of MEDIUM criticality -storing, accessing, processing information that is:
classified SENSITIVE, or
has a MEDIUM Integrity assessment, or
has a MEDIUM Availability assessment- must undergo a yearly independent internal audit of the information security control environment against the requirements of ISO 27001:2013
- the data custodian must be at the Director level or higher
- Information assets that are of LOW criticality - storing, accessing, processing information that is:
classified OFFICIAL, or has a LOW Integrity assessment, or has a LOW Availability assessment
must undergo a yearly audit of the information security control environment against the requirements of ISO 27001:2013
Reporting
- Criticality levels for each information asset / group of information assets (wherever applicable) must be provided by the identified data custodian to the Director-General through the Information Security Steering Committee within 30 days of the date that this policy was signed.
- An assurance report for each information asset/group of information assets (wherever applicable) must be provided annually on 1 September to the Director-General through the Information Security Steering Committee.
- The assurance report must be countersigned by the assurance assessor (internal audit / external assessor) and the information asset custodian
- Policy initiation
- Initial assurance reports for high criticality assets should be provided by the data custodian within 100 days (for example) of the date that this policy was signed;
- Initial assurance reports for medium criticality assets should be provided by the data custodian within 200 days (for example) of the date that this policy was signed; and
- Initial assurance reports for low criticality assets should be provided by the data custodian within 300 days (for example) of the date that this policy was signed.
Signed
Director General
accountable officer for <<Department>>
Date : DD/MM/YYYY